As the digital phase of survival has both advantages and disadvantages the risks held within the usage of digital products, make us a scape goat in the eyes of cyber criminals. The need to analyse such malicious acts is important for the digital platform to gain its trust among the masses. Thus, setting up Cybersecurity has emerged imperative for the protection of data from the hands of unauthorised actors.
Andrew Shikiar, Chief Marketing Officer and Executive Director of FIDO Alliance, states the need to look beyond cybersecurity training and focus on the authentication methods adopted to defend against hacking attacks. He also elaborates on how these methods go beyond security to provide users with a seamless login experience, a standard that is now expected of all.

Please give us a few instances where passwords and multi-factor authentication have failed.
Passwords are no longer sufficient in meeting the challenge of keeping critical information secure, and businesses must move away from them to ensure cybersecurity. The average consumer has almost 200 pairs of usernames and passwords, which is challenging to remember and keep track of. As such, most people tend to reuse the same passwords, or minor variations of a few passwords. Unsurprisingly, these poorly managed, easily guessed, or stolen passwords are behind about 80 percent of data breaches. One of the attacks which threat actors of the recent SolarWinds attack used to successfully infiltrate corporate networks, was in fact, password guessing.
As data breaches get increasingly severe, it’s become clear that passwords are more a liability than security. In recent years, multi-factor authentication (MFA) was introduced. With MFA, another element such as an OTP other than the password itself, is needed to authenticate the user, and these methods were thought to be ‘bullet-proof’ as there is an additional layer of security. However, password-based MFA can still be compromised. A recent case of financial crime in Singapore saw bad actors stealing about S$500,000 through fraudulent credit card transactions using one-time passwords, the very same additional layer of security we thought would keep these threats out.
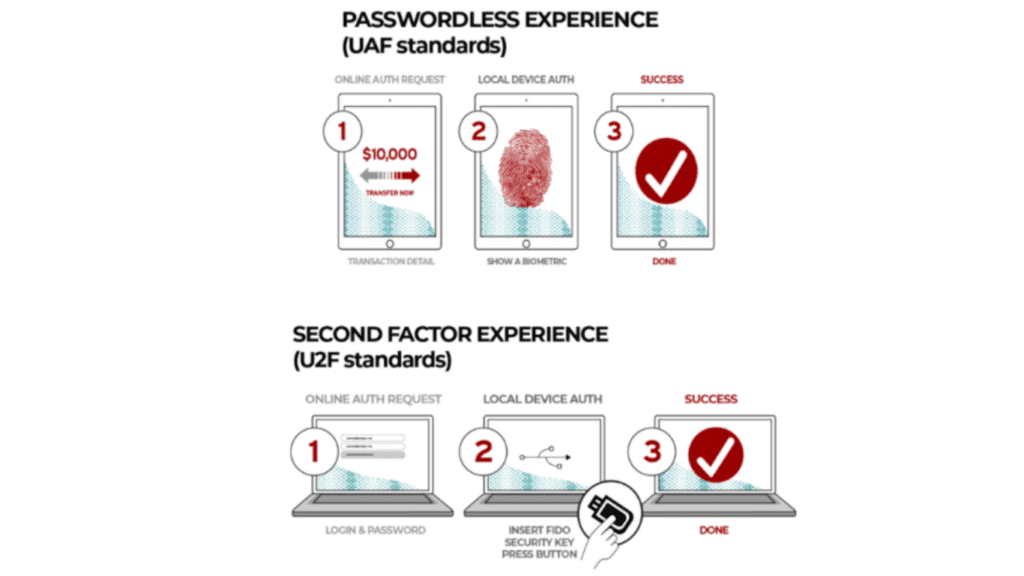
What is the common thread between ‘traditional’ passwords and MFA one-time passwords? Both are knowledge-based secrets that sit on a server, which can be stolen or manipulated from users by remote attackers and then reused through credential stuffing attacks. This raises the importance of enhanced, secure online authentication mechanisms that do not rely on passwords or other server-side credentials, but instead rely on possession-based factors.
As an expert in cybersecurity, what are your observations in this post-pandemic period, what have you experienced during the pandemic and what was it like before the pandemic?
While cyberattacks have long been rampant even before the pandemic, the situation has intensified. Lockdowns and movement control measures have forced businesses to quickly adapt and ‘go digital’ to run more efficiently and effectively. With organizations increasingly relying on cloud services and employees connected to the corporate network using multiple devices, a wider attack surface area of decentralized work environments is now open for cybercriminals to exploit.
Having to rapidly shift to remote or hybrid work also meant that businesses did not have the luxury of time to build the proper cyber defenses. To this end, cybercriminals have been quick to act as they ramped up their attacks and preyed on people’s anxieties and uncertainties. In fact, cybercrime is up 600 percent as a result of the COVID-19 pandemic in 2020. There is clearly more that needs to be done to protect against these attacks, and one obvious way forward is to evolve authentication methods to make sure malicious actors are kept out.
Do tell us about FIDO Alliance and its services and activities in detail.
The FIDO Alliance is an open industry association founded in 2012 with the goal of developing open industry standards for simpler, stronger authentication, while addressing the problems users face with managing multiple usernames and passwords.
FIDO promotes the development and use of standards for authentication and device attestation. This includes addressing the lack of interoperability among various authentication technologies and promoting global standards that make it easier for consumers to use, and easier for service providers to deploy and manage.
Today, the Alliance has over 250 member and partner organizations around the world, and its authentication standards are supported in platforms and products from various industry leaders such as Apple, Google, Microsoft and Samsung, and have been utilized to secure consumer logins for services from companies such as Facebook, Twitter, eBay, LINE, and NTT DOCOMO, as well as from the aforementioned platforms. For instance, FIDO2 security keys are one of the alternative authentication options supported by Microsoft, following the company’s latest move to remove passwords completely.
Tell us about your association with Google, GitHub and Facebook.
Google, Github and Facebook are just three of the many organisations that have implemented FIDO’s standards in their services.
Google, for instance, saw impressive outcomes following their internal implementation of FIDO U2F security keys. According to the company, there has not been a successful phishing attack against its 85,000+ employees since acquiring of these physical security keys. Google has expanded upon this to enable any user to protect their G Suite accounts with FIDO Authentication.
Github, too, has built FIDO Authentication into their authentication system in order to eradicate the necessity of passwords for login, while Facebook users can leverage FIDO Authentication to enable simpler, stronger, second-factor authentication.
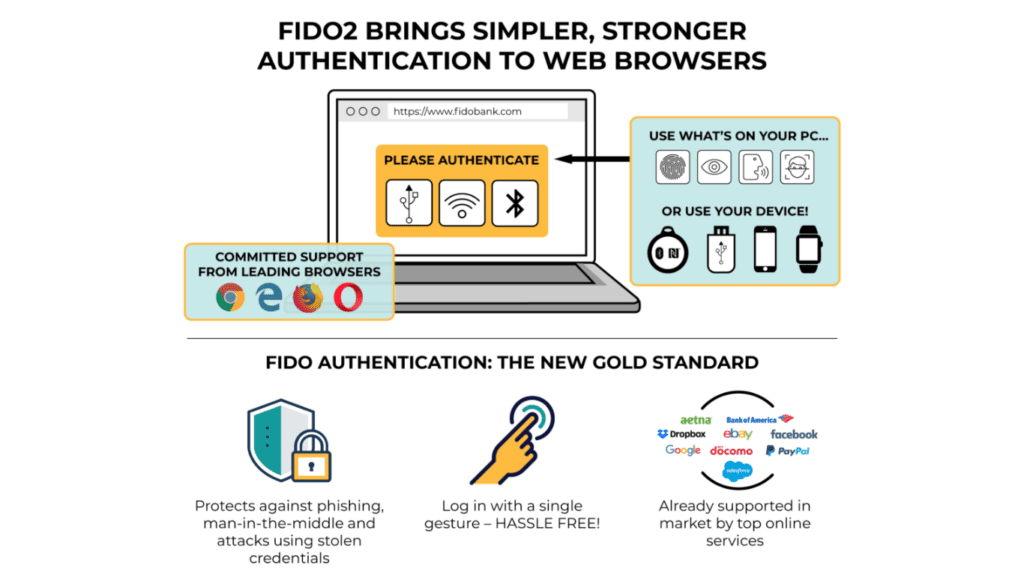
Virtually, every modern device and web browser now supports FIDO Authentication, and these standards are already used by various companies as part of their multi-factor integrated solutions, making it easier for users to log in and also harder for hackers to steal information. This allows users to have a more consistent experience across all their devices and offers them more control during their logins.
What is cryptographic secure authentication? How does it work?
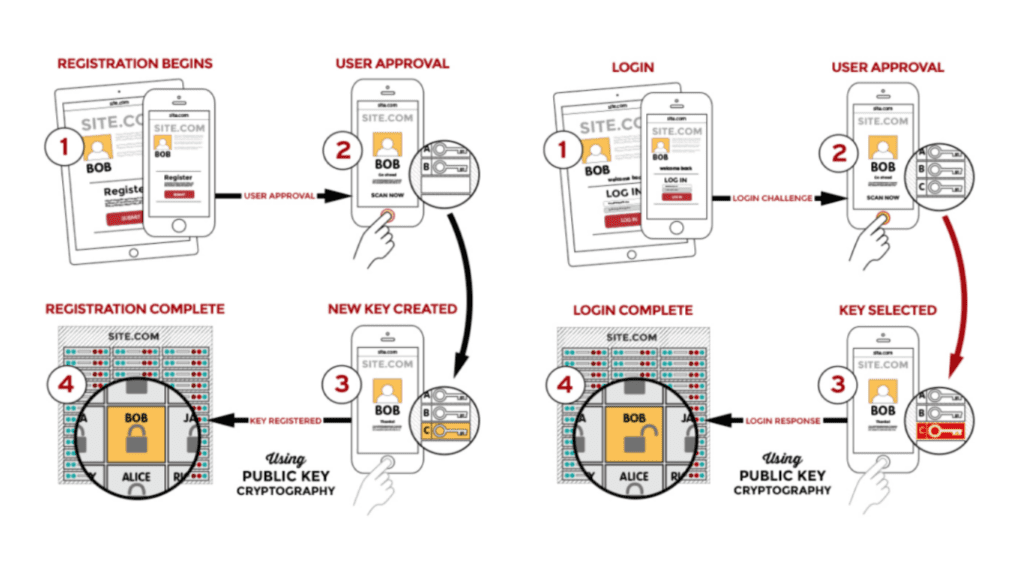
Cryptographic secure authentication or advanced public key cryptography techniques help to create a more seamless and secure experience for users. For a start, public key cryptography offers a layer of security that passwords lack. While passwords can be guessed, stolen, or hacked, key cryptography mitigates that risk by separating the information into two separate segments or keys.
The process is straightforward. When a user registers with an online service, specific information such as an authorized email or mobile phone number will be registered with the online service as the public key. These public keys are then used to verify its counterpart, the private key, which is stored securely on the user’s device in a two-step authentication method that ensures that identities are verified, guarding the information from unauthorized revelation and access.
FIDO’s standards are designed around public key cryptography, and this means that login information cannot be intercepted by hackers as it never leaves the local device. Furthermore, it enhances user control and eliminates the concern of account takeovers during logins. While public key cryptography, in itself, is not new, what is unique about FIDO’s approach is the focus on ease of use. With FIDO Authentication, users just need to make a single gesture with a device, such as a smartphone, laptop or security key to log into services and applications.
More importantly, it frees users from the hassle of remembering or typing passwords, leading to a better user experience. With this industry standard, users will also be able to login using the same feature they use to activate their devices, such as a fingerprint scan or facial recognition.
What is the difference and the challenge you face when you implement an authentication technology for the government and for the business houses?
The ability to prove one’s identity is increasingly recognized as the basis for the delivery of a range of services via web or mobile applications that require proof of identity. Authentication is critical to enabling secure delivery of digital identity services, which promotes efficiency gains, financial savings, social inclusion and access to basic services and rights.
The main difference and consideration when implementing a government authentication solution for citizen services would be that of accessibility. Given that any solution proposed must serve the entire population, the solution must be inclusive, and cannot exclude the disadvantaged, whether by geography or financial means. Citizens must be able to leverage their pre-existing devices, whereas in an enterprise setting, an IT administrator may choose to distribute FIDO security keys. Regardless, any authentication solution must guarantee a positive and convenient user experience and invoke a high level of trust. Both the private and public sector must embrace this shift, and ultimately, strike the balance between security and usability.






